Mateusz Slodkowski/SOPA Images/LightRocket via Getty Images
Researchers on Wednesday said they found fake apps in Google Play that masqueraded as legitimate ones for the Signal and Telegram messaging platforms. The malicious apps could pull messages or other sensitive information from legitimate accounts when users took certain actions.
An app with the name Signal Plus Messenger was available on Play for nine months and had been downloaded from Play roughly 100 times before Google took it down last April after being tipped off by security firm ESET. It was also available in the Samsung app store and on signalplus[.]org, a dedicated website mimicking the official Signal.org. An app calling itself FlyGram, meanwhile, was created by the same threat actor and was available through the same three channels. Google removed it from Play in 2021. Both apps remain available in the Samsung store.
Both apps were built on open source code available from Signal and Telegram. Interwoven into that code was an espionage tool tracked as BadBazaar. The Trojan has been linked to a China-aligned hacking group tracked as GREF. BadBazaar has been used previously to target Uyghurs and other Turkic ethnic minorities. The FlyGram malware was also shared in a Uyghur Telegram group, further aligning it to previous targeting by the BadBazaar malware family.
Signal Plus could monitor sent and received messages and contacts if people connected their infected device to their legitimate Signal number, as is normal when someone first installs Signal on their device. Doing so caused the malicious app to send a host of private information to the attacker, including the device IMEI number, phone number, MAC address, operator details, location data, Wi-Fi information, emails for Google accounts, contact list, and a PIN used to transfer texts in the event one was set up by the user.
Advertisement
The following screenshot shows the information in transit from the infected device to the attacker server:
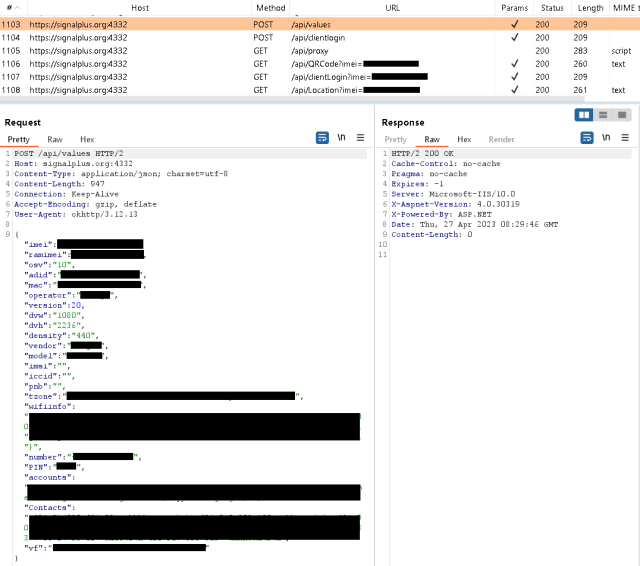 Enlarge / BadBazaar uploading device information to its C&C server.
Enlarge / BadBazaar uploading device information to its C&C server.
ESET
Signal Plus also abused a legitimate Signal feature that links the device running signal to a desktop or iPad so that users can send and receive texts across a wider range of devices. The linking process requires a user to download the desktop or iPad app and, once installed, use it to display a QR code that links to a unique key, such as sgnl://linkdevice?uuid=fV2MLK3P_FLFJ4HOpA&pub_key=1cCVJIyt2uPJK4fWvXt0m6XEBN02qJG7pc%2BmvQa. Signal Plus represents the first known case of an app spying on a victim’s Signal communications by secretly auto-linking the compromised device to the attacker’s Signal device.
ESET researcher Lukas Stefanko wrote:
Signal Plus Messenger can spy on Signal messages by misusing the link device feature. It does this by automatically connecting the compromised device to the attacker’s Signal device. This method of spying is unique, as we haven’t seen this functionality being misused before by other malware, and this is the only method by which the attacker can obtain the content of Signal messages.
BadBazaar, the malware responsible for the spying, bypasses the usual QR code scan and user click process by receiving the necessary URI from its C&C server, and directly triggering the necessary action when the Link device button is clicked. This enables the malware to secretly link the victim’s smartphone to the attacker’s device, allowing them to spy on Signal communications without the victim’s knowledge, as illustrated in Figure 12.
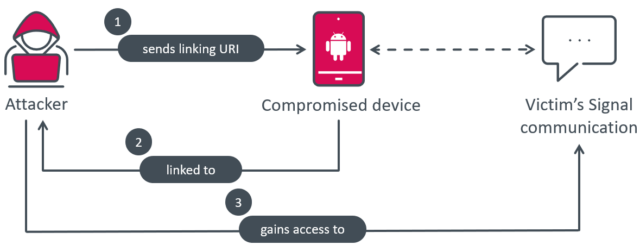 Enlarge / Mechanism of linking the victim’s Signal communications to the attacker.
Enlarge / Mechanism of linking the victim’s Signal communications to the attacker.
ESET
ESET Research has informed Signal’s developers about this loophole. The encrypted messaging service indicated that threat actors can alter the code of any messaging app and promote it in a deceptive or misleading manner. In this case, if the official Signal clients were to display a notification whenever a new device is linked to the account, the fake version could simply disable that code path to bypass the warning and hide any maliciously linked devices. The only way to prevent becoming a victim of a fake Signal—or any other malicious messaging app—is to download only official versions of such apps, only from official channels.
During our research, the server hasn’t returned to the device a URI for linking, indicating this is most likely enabled only for specifically targeted users, based on the data previously sent by the malware to the C&C server.
In a statement, Signal Foundation President Meredith Whittaker wrote:
Advertisement
We’re glad that the Play Store took this pernicious malware masquerading as Signal off their platform, and we hope they do more in the future to prevent predatory scams via their platform.
We’re deeply concerned for anyone who trusted and downloaded this app. We urge Samsung and others to move rapidly to remove this malware.
The discovery of this capability has largely gone unnoticed until now. It underscores the importance of downloading only the legitimate version of Signal and periodically checking Settings > Linked Devices to ensure no unrecognized devices appear.

