In the interest of combating ransomware and other malware, Microsoft is planning a major change in how its Office software handles macros: when files that use macros are downloaded from the Internet, those macros will now be disabled entirely by default. Current versions of the software offer an alert banner on these kinds of files that can be clicked through, but the new version of the banner offers no way to enable the macros.
The change will be previewed starting in April in Office version 2203, before being rolled out to all users of the continuously updated Microsoft 365 version of Office starting in June. The change will also be enabled for all currently supported standalone versions of Office, including versions 2021, 2019, 2016, and 2013. The Mac, iOS, Android, and web versions of Office won’t be affected.
Office can track which macros were downloaded from the Internet or from a networked share using a “Zone.Identifier” tag, at least when the file is saved to an NTFS volume. This so-called “mark-of-the-web” (MOTW) is already used in Office—if you’ve ever downloaded a document or spreadsheet and been informed that editing has been disabled by default, thank an MOTW. When Office sees a mark-of-the-web tag, the program opens that file in read-only Protected View mode just in case the file is malicious.
Advertisement
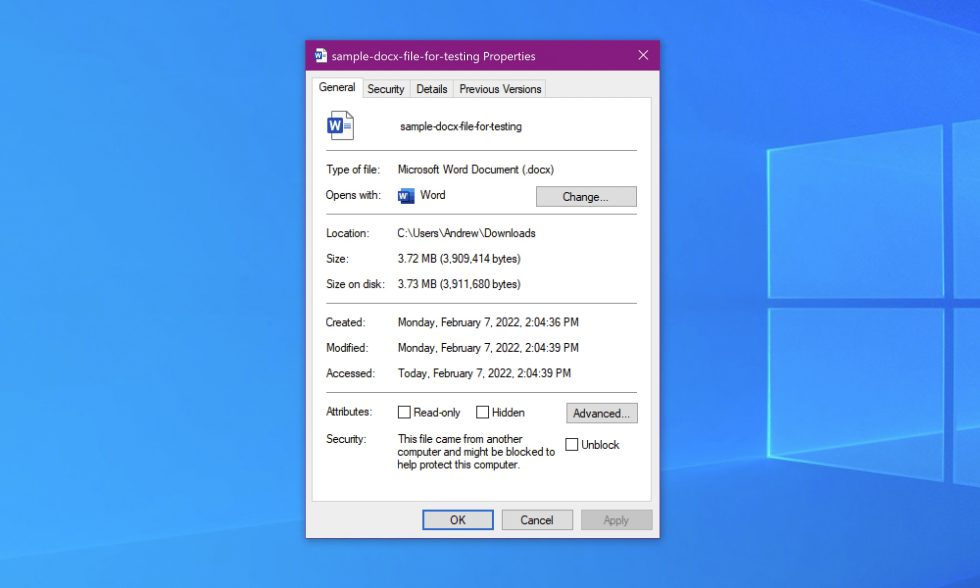 Enlarge / Clicking the “unblock” button here can remove the mark-of-the-web and re-enable VBA macros.
Enlarge / Clicking the “unblock” button here can remove the mark-of-the-web and re-enable VBA macros.
Andrew Cunningham
If users really want to, they will still be able to use these macros relatively easily. Open the properties for any Internet-downloaded file, and you can click an “unblock” button that removes the mark-of-the-web tag. As with so many security improvements, the change is not about making things impossible to do so much as it is about putting up ankle-height fences to protect users from accidental clicks or simple mistakes.
Organizations that rely on macros will also be able to change this setting via Group Policy. The organizations can do so by placing files with macros in “Trusted Locations” or by digitally signing their macros.

